Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
IT, cyber security tutorials and how-to content

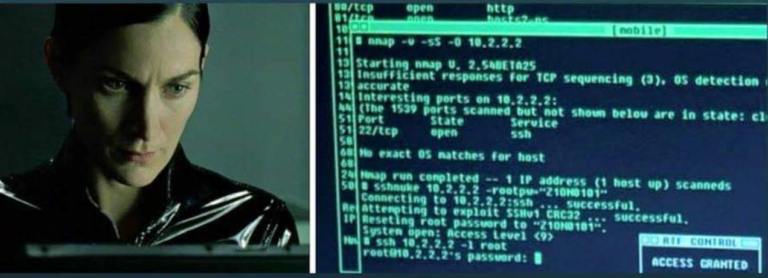
Active information gathering is the foundation for the network mapping step. As we discussed in the active information gathering post, NMAP is one of the common swiss-amry knife tools for network-based information gathering. When an attacker collects enough information about…

We started to explain passive information-gathering techniques in the previous post. Passive information gathering consists of techniques that generally leave no trace at the target about the attacker. However, these lack in collecting information about the target. In this post,…

Our previous post discussed critical steps in hacking/penetration testing. The first step is the information-gathering step. Information gathering is essential for a tester because initial data about the target(s), perimeter security details, public-facing services, and many more used technology details…


According to Offensive Security, Kali Linux is a special Debian distribution designed for various cybersecurity professions, including penetration testing, digital forensics, and malware analysis. A more detailed explanation can be found on the Offensive Security website. Yet Another Kali Installation?…