Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Information technology related blog posts

In this post we walk through hacking steps of a HackTheBox machine “UPDOWN”. This machine is UNIX based machine and according to HTB users hardness is medium. We considered that the step-by-step solution of this machine is helpful for pentesters.

In this post we explained two vulnerability analysis tools; Tanable Nessus and OpenVas. Overall, we explain installation and proper start of the two tools.

In this post, we walk through a HackTheBox machine, “Explore”. This machine is an ANDROID-based machine, and according to HTB users, hardness is easy. But we go over this machine’s step-by-step solution, which is useful for starters. Let’s begin. NMAP…
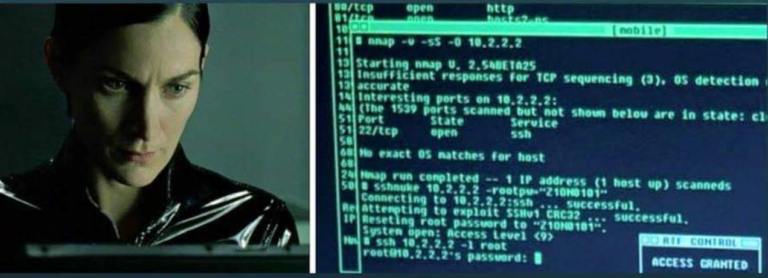
Active information gathering is the foundation for the network mapping step. As we discussed in the active information gathering post, NMAP is one of the common swiss-amry knife tools for network-based information gathering. When an attacker collects enough information about…

We started to explain passive information-gathering techniques in the previous post. Passive information gathering consists of techniques that generally leave no trace at the target about the attacker. However, these lack in collecting information about the target. In this post,…

Our previous post discussed critical steps in hacking/penetration testing. The first step is the information-gathering step. Information gathering is essential for a tester because initial data about the target(s), perimeter security details, public-facing services, and many more used technology details…

According to Offensive Security, Kali Linux is a special Debian distribution designed for various cybersecurity professions, including penetration testing, digital forensics, and malware analysis. A more detailed explanation can be found on the Offensive Security website. Yet Another Kali Installation?…