Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

In this post we tried to provide an overview of an hacking / pentesting activity against enterprise-level networks in nine steps.
There are two common cyber attack tactics, techniques, and procedures (TTPs). Lockheed Martin, The Cyber Kill Chain, and MITRE | ATT&CK Framework. ATT&CK framework is a living classification for common cyber-attacks and hacker TTPs. The Cyber Kill Chain has seven subcategories. At the time of writing, ATT&CK has 14 subcategories.
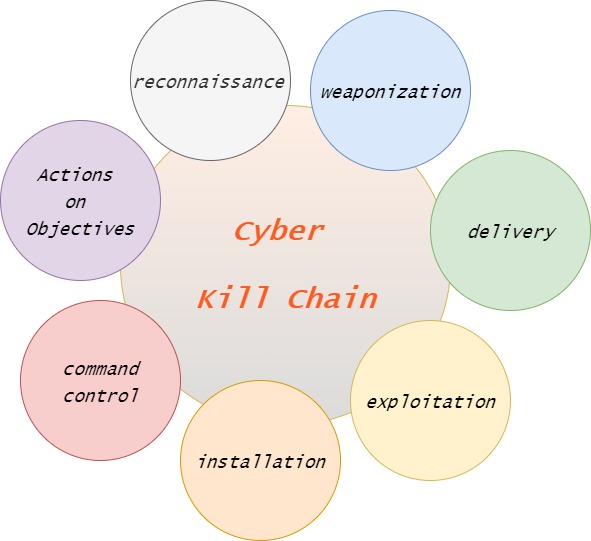

Cyber Kill Chain is for conducting red team operations or hacking activities against target(s). Mitre ATT&CK is the categorization of encountered cyber threats. We will try to specify our custom categorization in light of the Cyber Kill Chain and the focus on enterprise-level networks.
We structured nine steps for black box testing or hacking by putting Lockheed Martin’s The Cyber Kill chain our focus. In this post, we give short descriptions of each step, and we will explain each step in detail in the following posts. One can comprehend that each step requires a broad description. Each step has native techniques and tools to go over. To keep this blog post concise and understandable, we have gone over them separately.
Information Gathering
Information gathering can be passive or active. In passive information gathering, an attacker tries to find IP address sub-nets, domain names, DNS records, e-mail accounts and client software. In addition to these an attacker tries to collect information by using search engines. In active information gathering, an attacker tries to discover network and security systems. They try to fingerprint DNS, discover WAF, detect IPS in active information gathering.
Network Mapping
If an attacker collects enough information about the target, then they try to create a network mapping of the target. Network mapping is closely related with active information gathering.
Vulnerability Identification
Vulnerabilities are lacks on assets. When they are exploited they let an attacker to flee, by-pass security systems and let them to gain access.
Threat is either human or nature related incidents which can adversely effect organizations or networks. Vulnerabilities can be detected and assessed by using VA tools and software such as Nessus, OpenVAS.
Penetration
A successful penetration depends on a through information gathering and discovering vulnerabilities on the target. An attacker must try the most silent and reliable penetration technique to infiltrate networks, therefore this depends on a detailed, well planned enumeration and vulnerability discovery.
Gaining Access & Privilege Escalation
Penetration can be done for collecting internal data for defining more promising vulnerabilities about the target network and usually foundation for gaining access to services and assets in the network. After a successful penetration and gaining access to resources an attacker must seek ways to get administrative privileges. This way of leveraging permissions is called privilege escalation. For our perspective this is the heart of an cyber attack. After this step an attacker can gain unrestricted access to the valuable data and resources at the internal network.
Enumerating Further
Getting root password or capturing domain administrator account may seem enough for many. But networks have different systems which are to be found. For instance an active directory is valuable for IT, but blueprints of the upcoming product is valuable for the entire company. So an attacker should enumerate further by pivoting, lateral movement. After getting enough information, we should leave our tool (script, executable, system configuration) for further access to the system. In addition to that after enumerating further an attacker may want to exfiltrate data and skip following two steps.
Compromising Remote Users/Sites
Getting unrestricted access to a site may yield access to another remote sites. An attacker can use the captured credentials for hacking other remote sites and users to broaden their reach.
Maintain Access
As mentioned at the enumerating further step, an attacker needs to be persistent on the exploited systems. For meeting this goal they can create a backdoor, a malware or a system configuration. After doing one of these an attacker can access the system whenever her/she wants.
Covering Tracks (Report)
If these eight steps are done for penetration testing, then we create a report which shows detailed actions during the tests. Otherwise, an attacker should cover his actions either purging the log data or making them inaccessible.
In this post, in nine steps, we tried to provide an overview of a hacking / pen-testing activity against enterprise-level networks. Some steps may be skipped if target networks are known, if tests are gray-box, etc. I hope this is helpful for your offensive cyber security activities.
Emre Caglar Hosgor