Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

In my previous blog post, I delved into the critical importance of…

Importance of Computer Forensics Process In this post, we started the technical…

We will dive into the details of DFIR in this blog posts. Initially, we will explain why we require a forensic investigator and discuss legal issues, code of ethics in DFIR.

In this post we walk through hacking steps of a HackTheBox machine “UPDOWN”. This machine is UNIX based machine and according to HTB users hardness is medium. We considered that the step-by-step solution of this machine is helpful for pentesters.

In the previous post, we introduced Digital Forensics and Incident Response (DFIR)…

At the beginning of the DFIR blog series, we would like to…

In this post, we walk through the hacking steps of a HackTheBox machine, "Timelapse." This machine is WINDOWS-based, and according to HTB users, hardness is easy. This box is running Active Directory services...

In this post, we walk through the hacking steps of a HackTheBox machine “Trick”. This machine is UNIX based machine and according to HTB users hardness is easy.

In this post we explained two vulnerability analysis tools; Tanable Nessus and OpenVas. Overall, we explain installation and proper start of the two tools.

In this post, we walk through a HackTheBox machine, “Explore”. This machine…
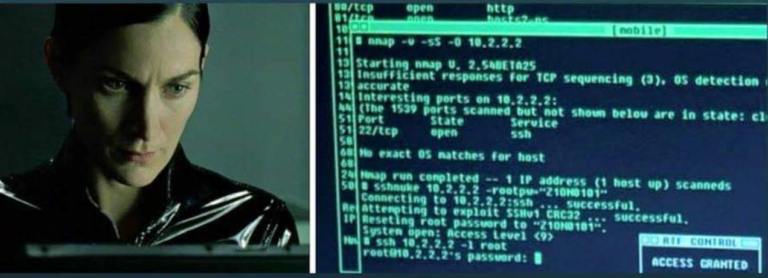
Active information gathering is the foundation for the network mapping step. As…

We started to explain passive information-gathering techniques in the previous post. Passive…

Our previous post discussed critical steps in hacking/penetration testing. The first step…

In this post we walk through steps of a HackTheBox machine “Pikaboo”.…

In this post we walk through the steps of a HackTheBox machine “Knife”.…

In this post we walk through a solution of a HackTheBoxmachine “Love”.…

In this post we walk through haking steps of a HackTheBox machine…

In this post we tried to provide an overview of an hacking / pentesting activity against enterprise-level networks in nine steps.

According to Offensive Security, Kali Linux is a special Debian distribution designed…